
JavaScript must be enabled in order to use this site.
YARN only: Create the yarn keytab file, which contains an entry for the yarn principal. This keytab file is used for the ResourceManager and NodeManager. Kadmin: xst -k yarn-unmerged.keytab yarn/fully.qualified.domain.name; Create the http keytab file, which contains an entry for the HTTP principal. To create a keytab file: On the domain controller server, create a user account named control- in the Active Directory Users and Computers snap-in. If you want to use the AES256-SHA1 encryption algorithm, do the following in the Active Directory Users and Computers snap-in: Open the properties of the created account.
Please enable JavaScript in your browser and refresh the page.
This is the documentation for Cloudera Enterprise 5.11.x. Documentation for other versions is available at Cloudera Documentation.
Generate Keytab File Mac
If your version of Kerberos does not support the Kerberos -norandkey option in the xst command, or if you must usekadmin because you cannot use kadmin.local, then you can use the following procedure to create Kerberos keytab files. Using the-norandkey option when creating keytabs is optional and a convenience, but it is not required.
Important:For both MRv1 and YARN deployments:On every machine in your cluster, there must be a keytab file for the hdfs user and a keytab file for the mapred user. The hdfs keytab file must contain entries for the hdfs principal and an HTTP principal, and the mapred keytab file must contain entries for the mapred principal and an HTTP principal. On each respective machine, the HTTP principal will be the same in both keytabfiles.
In addition, for YARN deployments only:On every machine in your cluster, there must be a keytab file for the yarn user. The yarn keytab file must contain entries for the yarn principal and an HTTPprincipal. On each respective machine, the HTTP principal in the yarn keytab file will be the same as the HTTP principal in the hdfs and mapred keytab files.
For instructions, see To create the Kerberos keytab files.
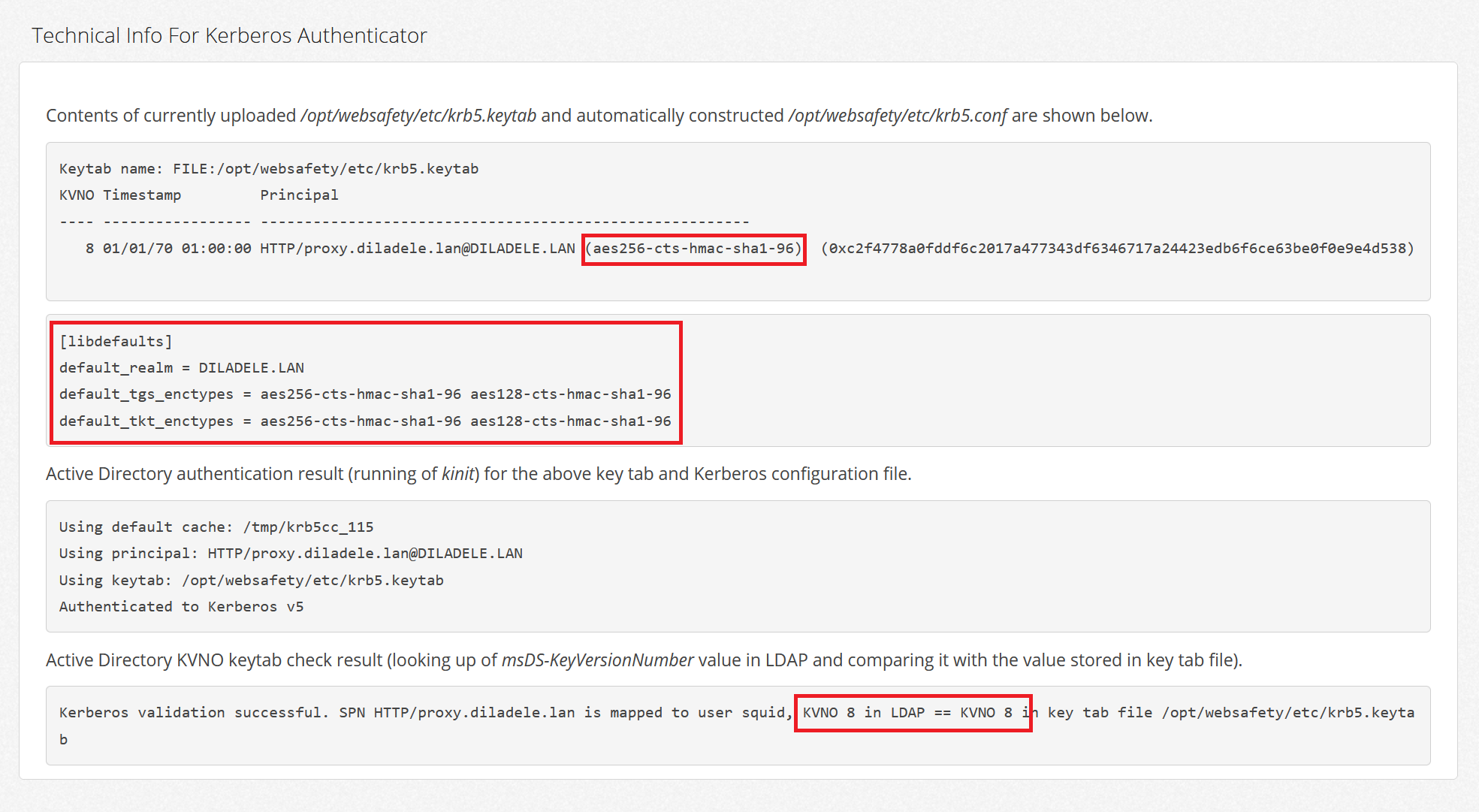
Note:These instructions illustrate an example of creating keytab files for MIT Kerberos. If you are using another version of Kerberos, refer to your Kerberos documentation for instructions.You can use either kadmin or kadmin.local to run these commands.

To create the Kerberos keytab files
Do the following steps for every host in your cluster, replacing the fully.qualified.domain.name in the commands with the fully qualified domain name ofeach host:
- Create the hdfs keytab file, which contains an entry for the hdfs principal. This keytab file is used for the NameNode,Secondary NameNode, and DataNodes.
- Create the mapred keytab file, which contains an entry for the mapred principal. If you are using MRv1, the mapred keytab file is used for the JobTracker and TaskTrackers. If you are using YARN, the mapred keytab file is used for the MapReduce Job HistoryServer.
- YARN only: Create the yarn keytab file, which contains an entry for the yarn principal. Thiskeytab file is used for the ResourceManager and NodeManager.
- Create the http keytab file, which contains an entry for the HTTP principal.
- Use the ktutil command to merge the previously-created keytabs:
This procedure creates three new files: hdfs.keytab, mapred.keytab and yarn.keytab. Thesefiles contain entries for the hdfs and HTTP principals, the mapred and HTTPprincipals, and the yarn and HTTP principals respectively.
- Use klist to display the keytab file entries. For example, a correctly-created hdfs keytab file should look something likethis:
- To verify that you have performed the merge procedure correctly, make sure you can obtain credentials as both the hdfs and HTTP principals using the single merged keytab:
If either of these commands fails with an error message such as 'kinit: Key table entry not found while getting initial credentials', then something hasgone wrong during the merge procedure. Go back to step 1 of this document and verify that you performed all the steps correctly.
- To continue the procedure of configuring Hadoop security in CDH 5, follow the instructions in the section To deploy the Kerberos keytab files.
Next: Some Advice about Secure Hosts,Previous: Server Configuration Files,Up: UNIX Application Servers
4.3.3 The Keytab File
All Kerberos server machines need a keytab file, called/etc/krb5.keytab, to authenticate to the KDC. The keytab file isan encrypted, local, on-disk copy of the host's key. The keytab file,like the stash file (Create the Database) is a potentialpoint-of-entry for a break-in, and if compromised, would allowunrestricted access to its host. The keytab file should be readableonly by root, and should exist only on the machine's local disk. Thefile should not be part of any backup of the machine, unless access tothe backup data is secured as tightly as access to the machine's rootpassword itself.
In order to generate a keytab for a host, the host must have a principalin the Kerberos database. The procedure for adding hosts to thedatabase is described fully in the “Adding or Modifying Principals”section of the Kerberos V5 System Administrator's Guide. See Create Host Keys for the Slave KDCs. for a brief description.) The keytab is generated by running kadmin and issuing thektadd command.
Cached
For example, to generate a keytab file to allow the hosttrillium.mit.edu to authenticate for the serviceshost, ftp, and pop, the administratorjoeadmin would issue the command (ontrillium.mit.edu):
If you generate the keytab file on another host, you need to get a copyof the keytab file onto the destination host (trillium, in theabove example) without sending it unencrypted over the network. If youhave installed the Kerberos V5 client programs, you can useencrypted rcp.